-
-
Notifications
You must be signed in to change notification settings - Fork 208
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
VPN Overview Rewrite #2117
VPN Overview Rewrite #2117
Conversation
✅ Deploy Preview for privacyguides ready!
To edit notification comments on pull requests, go to your Netlify site configuration. |
|
What are your thoughts on mentioning Multi-Party Relays (MPRs)? |
|
We should look into them more and probably mention them. The main issue is that the only two commercial options I know of are the two mentioned in that blog post (the blog author's and iCloud), but since Tor is also technically a Multi-Party Relay, it would be good to outline the different threat models they serve compared to traditional VPNs. |
|
I also wouldn't be opposed to writing something about DVPNs and mentioning https://www.ivpn.net/privacy-guides/comparing-dvpns-centralized-vpns-privacy-protection/ and the risks with them and also why we don't recommend them. They do come up from time to time and it would be nice to be able to point to a particular section. While that article is by a centralized VPN service, it does raise some very important points being that:
|
|
@jonaharagon The problem with all of MPRs (two-hop) is that they require some server (or servers) which relay the traffic and someone has to pay for those servers and their associated bandwidth. iCloud Private Relay and most VPNs are not free, so the user is the one who pays. Tor (three hops) is different: instead of having a single provider such as Apple or your VPN provider, Tor servers are operated by the Tor community on a volunteer basis and are free to users. While the problem with tor is the 1st and 3rd nodes with MPRs (two hops), you have to trust the both relay companies to not correlate/share information about connected user. @dngray sounds good. It is also worth to mention https://educatedguesswork.org/posts/public-wifi/ (biggest selling point for VPNs) |
Well, this is not a problem, all of our VPN recommendations are paid services, as they should be. @dngray it's worth noting that I think "dVPNs" are a different sort of service than the multi-hop VPNs @quackerex was referring to. |
|
This pull request has been mentioned on Privacy Guides. There might be relevant details there: |
I actually meant that you have to pay using your credit card to use these commercial MPRs. |
Egress layer can route traffic through multiple servers. So they have to correlate traffic between multiple server providers (In this case Akamai, Cloudflare, and Fastly). I see this as impossible scenario. It is also important to point out that ODoH is also used in MPRs which is similar to DNS over Tor. |
docs/basics/vpn-overview.md
Outdated
| @@ -83,6 +83,10 @@ You should also be wary that many VPN review sites are merely advertising vehicl | |||
|
|
|||
| [Our VPN Recommendations](../vpn.md){ .md-button } | |||
|
|
|||
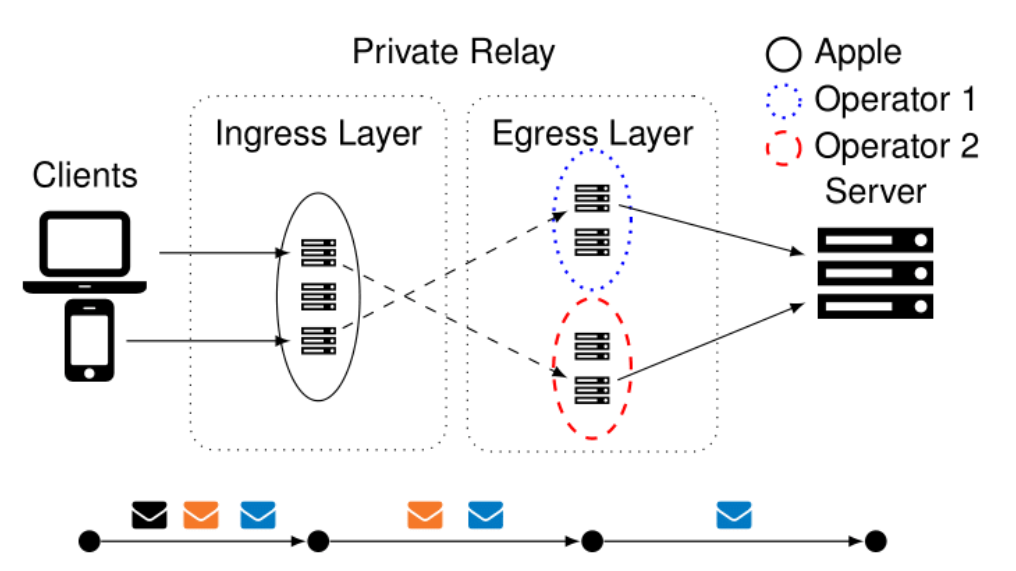
| ## Multi-Party Relays | |||
|
|
|||
| Multi-Party Relays use multiple nodes owned by different parties, such that no individual party knows enough to track you. This is the idea behind Tor, but now there are some paid services that try to emulate this model. | |||
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
I think it is important to highlight that web browsing with MPRs is on par with non-proxied, and sometimes even faster (this is not the case for Tor or VPNs ).
This is achieved using the MASQUE (Multiplexed Application Substrate over QUIC Encryption) specification standardized by the IETF.
docs/basics/vpn-overview.md
Outdated
|
|
||
| Encryption offered by VPN providers is between your devices and their servers. It guarantees that this specific link is secure. This is a step up from using unencrypted proxies where an adversary on the network can intercept the communications between your devices and said proxies and modify them. However, encryption between your apps or browsers with the service providers are not handled by this encryption. | ||
|
|
||
| In order to keep what you actually do on the websites you visit private and secure, you must use HTTPS. This will keep your passwords, session tokens, and queries safe from the VPN provider. Always check for the lock icon in your browser's URL bar to mitigate downgrade attacks like [SSL Strip](https://www.blackhat.com/presentations/bh-dc-09/Marlinspike/BlackHat-DC-09-Marlinspike-Defeating-SSL.pdf). |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
should probably just recommend HTTPS-only mode instead, no one is going to check little locks everywhere.
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
I think the lock icon is going the way of the dodo anyway.
Changes proposed in this PR:
closes #2118