-
-
Notifications
You must be signed in to change notification settings - Fork 11
Commit
This commit does not belong to any branch on this repository, and may belong to a fork outside of the repository.
Create 2024-11-13-musings-progressive-trust-lifecycle.md
- Loading branch information
Showing
1 changed file
with
137 additions
and
0 deletions.
There are no files selected for viewing
137 changes: 137 additions & 0 deletions
137
_posts/2024-11-13-musings-progressive-trust-lifecycle.md
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,137 @@ | ||
| --- | ||
| header: | ||
| overlay_color: "#00f" | ||
| overlay_filter: "0.35" | ||
| overlay_image: /images/blueprints.jpg | ||
| og_image: /images/musings-card.jpg | ||
| actions: | ||
| - label: "See All Musings" | ||
| url: /musings.html | ||
| tagline: "The Power of Progressive Trust" | ||
| title: "Musings of a Trust Architect: Building Trust in Gradients" | ||
| author: "Christopher Allen" | ||
| excerpt_separator: "<!--more-->" | ||
| classes: | ||
| - wide | ||
| categories: | ||
| - Musings | ||
| tags: | ||
| - Progressive Trust | ||
| - Trust | ||
| image: https://raw.githubusercontent.com/BlockchainCommons/www.blockchaincommons.com/master/images/musings.png | ||
| --- | ||
|
|
||
|
|
||
| **Progressive Trust**—it sounds a bit like something from a relationship advice column, right? But in the world of digital interactions, it’s actually a revolutionary model, one that moves us away from "all-or-nothing" choices into a more human, flexible way of establishing trust. Progressive Trust is about mirroring the natural ways we build trust in real life, adding depth and resilience to our digital interactions. | ||
|
|
||
| > "The basic idea behind progressive trust is to model how trust works in the real world"<br> | ||
| > —Christopher Allen, [Musings of a Trust Architect: Progressive Trust](https://www.blockchaincommons.com/musings/musings-progressive-trust/) (December 2022) | ||
| In real life, trust doesn’t happen at the click of a button. It’s a process. You don’t start a friendship, a business deal, or a marriage with complete openness or blind trust. Instead, [what you reveal is initially minimized](https://www.blockchaincommons.com/musings/musings-data-minimization/), and then trust builds up gradually. As we share experiences, we reveal more, bit by bit, learning through consistent responses from the other person. When it comes to digital relationships, whether they’re between people, devices, or other entities, why should things be any different? | ||
|
|
||
| ## Why Progressive Trust Matters Today | ||
|
|
||
| The internet didn’t start off so polarized. Back in the early days, you could slowly get to know people online, like on message boards or MUDs, where interaction was incremental and organic. But as commercialization took over, new online communities popped up with **restricted, binary models** of trust. Tech giants started telling us who to trust based on certificates or institutional endorsements, pushing people into a “trust or don’t trust” mindset. But this one-size-fits-all approach isn’t just impersonal. It’s risky. Without the gray area, we’re left with blind trust or total skepticism, with few options inbetween. | ||
|
|
||
| Enter Progressive Trust, which seeks to change that by **returning choice to the user**, letting individuals decide whom to trust and how much of themselves to reveal over time. It’s an effective way to enhance security and protect user agency, fitting seamlessly into decentralized systems like blockchain, where openness and security go hand in hand. Progressive Trust takes the online world back to a more natural process of gradual trust-building, transforming digital trust from a binary affair into something more organic. | ||
|
|
||
| ## The Progressive Trust Life Cycle | ||
|
|
||
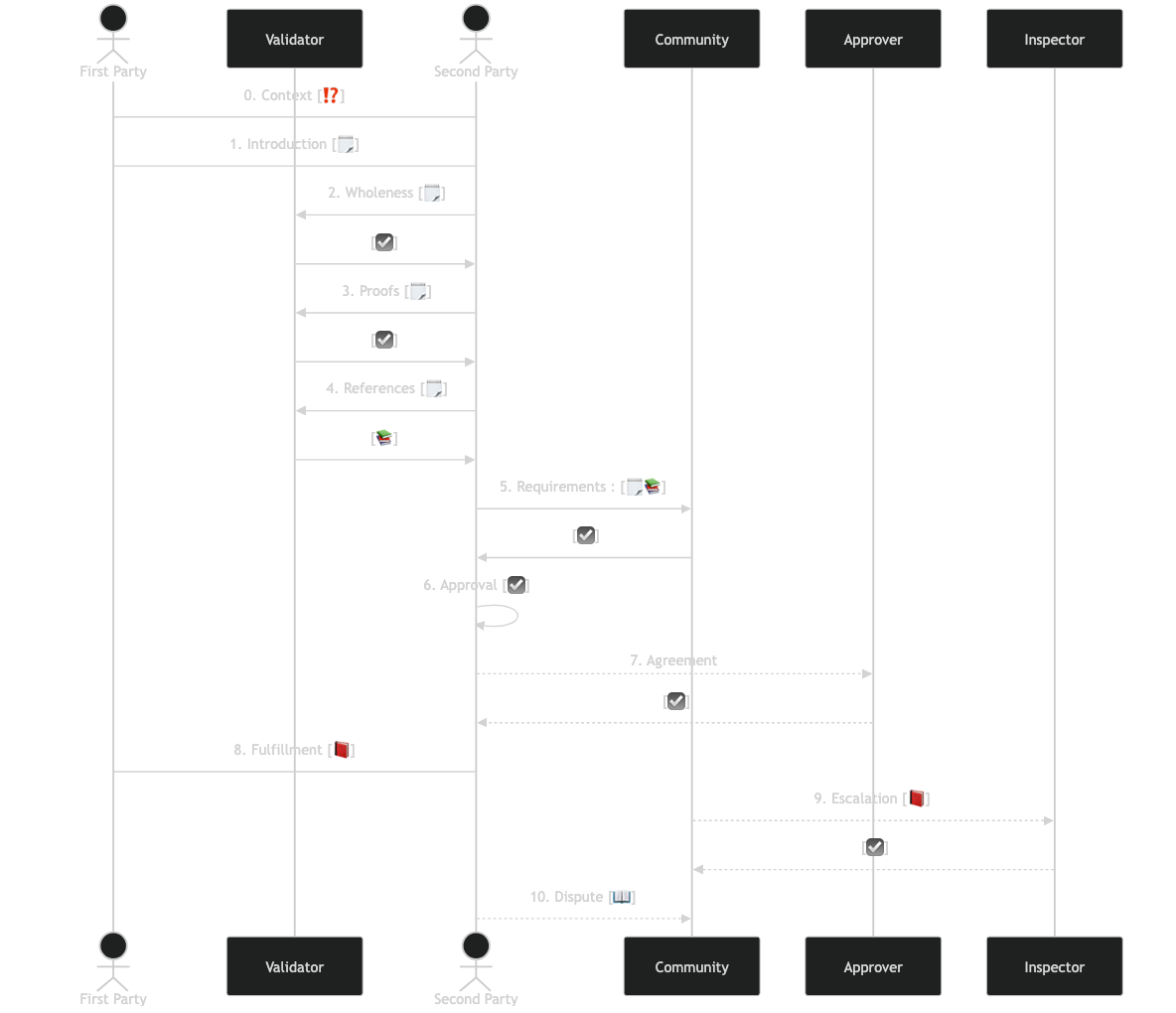
| Let’s break down the **Progressive Trust Life Cycle** into its key phases, each step building on the last and adding layers of trust over time. Think of it as a journey from cautious introduction to informed engagement, with each phase providing the groundwork for a stronger, more resilient trust model. These are the steps of progressive trust that are simultaneously automatic in the real world and often ignored in the digital world. | ||
|
|
||
| ### 0. **Context** – _Interaction Considered_ | ||
| The foundation of Progressive Trust begins with understanding the **Context** of an interaction. This sets the stage by establishing the purpose and parameters of the interaction, helping each party assess risk and feasibility. Before any data is exchanged or any commitments are made, each party considers the interaction's purpose, its goals, its potential benefits, and the risks involved. They also examine the setting in which the interaction takes place, ensuring that they understand the overall environment and any particular conditions that might impact their decision. | ||
|
|
||
| > *Example:* A homeowner, Hank, evaluates hiring a contractor for a kitchen remodel. He considers the financial costs, the importance of quality work, and the potential risks of inviting someone into his home for an extended period. The stakes of the scenario are sufficient to prompt Hank to engage in a Progressive Trust model, as opposed to a quick, one-off transaction. | ||
| This initial phase helps each side assess whether the potential stakes, such as financial or reputational risk, warrant a full, Progressive Trust approach or if simpler, lower-risk models could suffice. | ||
|
|
||
| ### 1. **Introduction** – _Assertions Declared_ | ||
| With the interaction context defined, both parties proceed with **Introduction**, where they each make initial declarations and claims. By sharing basic information, the parties set the groundwork for further scrutiny, while keeping sensitive details private or hidden (for now). | ||
|
|
||
| > *Example:* Hank meets Carla, the cabinet maker, at a social gathering and discusses his interest in remodeling his kitchen. Carla offers her business card and highlights her experience, expressing interest in working with him. This initial interaction is informal yet purposeful, establishing the first connection and introducing each party’s intentions. | ||
| This phase is an essential starting point for trust-building, as it allows each party to signal their intentions clearly and publicly, establishing a mutual understanding of what they aim to accomplish. | ||
| It does not involve extensive trust verification but instead creates a framework of transparency and expectation between the participants. | ||
|
|
||
| ### 2. **Wholeness** – _Integrity Assessed_ | ||
| Once an introduction has been established, both parties assess the **Wholeness** of the information shared. This phase involves evaluating the structural integrity of the data, ensuring that all critical pieces are complete and correctly formatted. Think of this as a quality check: verifying that foundational information is present, well-formed, and free from any immediate signs of corruption or tampering. | ||
|
|
||
| > *Example:* Hank checks Carla’s business card, noting that it includes her contractor license number and contact details. Carla, meanwhile, considers whether Hank’s job aligns with her skillset. Both use this phase to make sure the information they have about each other is coherent and free of red flags. | ||
| This phase creates the foundation for deeper verification by ensuring that each party’s data contributions are reliable at a surface level. Without verifying structural integrity, any future steps could rest on flawed or incomplete data, leading to potential misunderstandings or risks. | ||
|
|
||
| ### 3. **Proofs** – _Secrets Verified_ | ||
| With data integrity confirmed, the next step is **Proofs**, where parties delve into verifying the sources of the data. It’s a deeper level of validation, establishing the authenticity of the sources for each party’s assertions. That validation leverages modern technology such as digital signatures where possible, to minimize the risk of misrepresentation or fraud. | ||
|
|
||
| > *Example:* Hank calls a few of Carla’s previous clients, confirming that they exist, and the testimonials given to him are real. Similarly, Carla may ask for proof of Hank’s readiness to pay by confirming his budget or financial standing. | ||
| This phase confirms that both parties’ assertions are backed by a proof, to establish a more secure foundation for the interaction. | ||
|
|
||
| ### 4. **References** – _Trust Aggregated_ | ||
| Building on the established proofs, the **References** phase broadens trust by gathering endorsements, certificates, or additional validation from external sources. This step goes beyond just authenticating the source of any assertions. It's about gathering the good word from others, including testimonials, reviews, licenses, or certificates. Cryptographic methods may also be used to assure the validity of the references. Parties don't necessarily gather every reference: they collect until they feel they have enough corroborating information to proceed. | ||
|
|
||
| > *Example:* Hank checks Carla’s contractor license in a state registry and reads online reviews. Carla, in turn, verifies Hank’s reputation or credibility within her professional network, gaining confidence that his project is legitimate and that he can be trusted to honor financial commitments. | ||
| This phase provides a composite view of the other party’s trustworthiness based on diverse sources, making trust more holistic. It creates a comprehensive picture without oversimplifying the credibility of each party into a binary “yes” or “no.” | ||
|
|
||
| ### 5. **Requirements** – _Community Compliance_ | ||
| After personal and third-party validation, the parties consider whether the interaction meets broader **Community Standards and Requirements**. Here, each party assesses if the interaction complies with external guidelines, legal standards, or industry norms, which may vary by context. Compliance might involve revealing additional data, following guidelines for quality or safety, or meeting regulatory requirements, which helps each party feel confident that their involvement is appropriate and sanctioned. | ||
|
|
||
| > *Example:* Hank ensures that Carla’s contractor license and project quote meet legal requirements and industry standards, such as fair pricing and warranty expectations. Carla might consult her network or a local building authority to verify that Hank’s project is feasible and professionally compliant. | ||
| This phase adds another layer of credibility through its confirmation that the interaction aligns with expected practices and requirements. | ||
|
|
||
| ### 6. **Approval** – _Risk Calculated_ | ||
| With community compliance confirmed, each party calculates the risk of proceeding and provides a tentative **Approval**. This step involves a personal assessment, comparing the accumulated trust to any potential risks or liabilities. It’s a decision point where each party considers their own risk model and goals, assessing whether the interaction is likely to fulfill their needs without exposing them to undue harm. Approval may involve internal checks or may require formal documentation of agreed-upon terms. | ||
|
|
||
| > *Example:* Hank and Carla both review the project’s terms and risk factors, ensuring they feel comfortable with potential liabilities. When ready, they formalize their commitment by signing a contract, each confident that the project aligns with their risk model and is mutually beneficial. | ||
| This phase emphasizes that trust isn’t an all-or-nothing concept. It exists on a spectrum, and each party must decide if their level of trust is sufficient to continue. | ||
|
|
||
| ### 7. **Agreement** – _Threshold Endorsed_ (Optional) | ||
| In situations of higher stakes or complexity, the **Agreement** phase may require additional endorsements before proceeding. An Agreement phase is optional but valuable when external input can add layers of confidence, often through the endorsement of peers, family members, or other trusted figures. Threshold endorsements are vital in larger or more sensitive projects, ensuring that all necessary parties or authorities approve before moving forward. | ||
|
|
||
| *Example:* Hank might discuss the project with his family for added assurance, while Carla secures necessary permits from the city. Both parties use these endorsements to reinforce | ||
|
|
||
| This phase provides an extra level of validation, helping each party feel more secure in their decision to proceed. | ||
|
|
||
| ### 8. **Fulfillment** – _Interaction Finalized_ | ||
| **Fulfillment** is the phase where each party finally executes their commitments, bringing the project to life based on the trust established through previous steps. Fulfillment requires each party to act according to the rules they’ve set, adhering to any terms, standards, or expectations agreed upon earlier. | ||
|
|
||
| > *Example:* Carla completes the kitchen remodel, delivering quality work as per the contract. Hank, in turn, fulfills his financial commitment by making the payment. The project reaches its conclusion, satisfying both parties' expectations based on their prior trust-building efforts. | ||
| This phase represents the culmination of the trust-building process, where both sides honor their agreements and responsibilities. It’s a phase of action rather than evaluation, marking a key transition from planning to execution, after which the interaction is officially complete. | ||
|
|
||
| ### 9. **Escalation** – _Independently Inspected_ (Optional) | ||
| In high-stakes or sensitive interactions, the **Escalation** phase optionally introduces an independent, third-party inspection. This step allows an impartial reviewer to verify that each party’s work or commitments were met, ensuring that the final product aligns with the agreed-upon standards. An inspector may re-evaluate certain phases, especially compliance and fulfillment, confirming that all requirements were followed. | ||
|
|
||
| > *Example:* A city inspector reviews Carla’s remodel to ensure it complies with local building codes, giving Hank and Carla final confirmation that the project meets regulatory standards. | ||
| This phase helps protect each party, providing an additional level of assurance when risk is high or when the interaction has lasting implications. | ||
|
|
||
| ### 10. **Dispute** – _Independently Arbitrated_ (Optional) | ||
| If issues arise, the final, optional phase of **Dispute** involves resolving conflicts through independent arbitration. In cases where fulfillment does not meet expectations, each party may bring forth additional data or reveal previously concealed information to support their case. An arbitrator then assesses the evidence, reviewing both parties’ original commitments, agreements, and standards, to determine a fair resolution. | ||
|
|
||
| > *Example:* If a cabinet installed by Carla collapses, Hank may initiate a dispute to assess liability. An independent arbitrator reviews the contract, Carla’s compliance with installation standards, and any relevant inspection reports, ultimately deciding if Carla is responsible for repairs or damages. | ||
| _This phase safeguards both parties, providing a structured way to resolve disagreements that may impact future interactions or reputations._ | ||
|
|
||
|
|
||
| ## The Progressive Trust Life Cycle | ||
|
|
||
|  | ||
|
|
||
| ## Beyond Binary Trust: How Progressive Trust Can Transform the Internet | ||
|
|
||
| Progressive Trust offers a way to **return agency to individuals** in a world increasingly dominated by centralized systems. Instead of clicking “OK” on trust agreements handed down by big corporations, users regain control over who they trust and to what degree, over time. Imagine a digital ecosystem where browsers, websites, or social media platforms gradually allowed users to choose what information they revealed and what they kept private, based on their own evolving trust models. | ||
|
|
||
| ### From Gradients to Greatness | ||
|
|
||
| The vision for Progressive Trust goes beyond making interactions safer; it’s about bringing digital trust closer to real-world norms. With Progressive Trust, we’re not just building secure systems—we’re creating environments where people can **interact meaningfully and sustainably**, with digital relationships that grow stronger over time, just like in real life. Whether it’s in journalism, finance, wellness, or personal data sharing, the possibilities are endless when trust is no longer binary. | ||
|
|
||
| **Progressive Trust is hard, but it’s worth it.** It’s a mature model, one that can elevate our digital interactions by letting trust grow naturally. We’ve evolved this process over thousands of years in the physical world; now it’s time to bring the same wisdom to the online world. By embracing Progressive Trust, we’re not just keeping data safe; we’re building a digital space where people can **authentically connect and collaborate**, one step at a time. | ||
|
|
||
| --- | ||
|
|
||
| _For a more extensive discussion of this Life Cycle, including a look at the vocabulary and several more examples in different domains, see ["The Progressive Trust Life Cycle"](https://developer.blockchaincommons.com/progressive-trust/) on the Developer web pages. For more on progressive trust, see my 2004 [introduction of the concept](https://www.lifewithalacrity.com/article/progressive-trust/) and my more recent 2022 [musings on the topic](https://www.blockchaincommons.com/musings/musings-progressive-trust/)._ |