Alpine Linux image with nginx 1.23.4 (mainline) with HTTP/3 (QUIC), TLSv1.3,
0-RTT, HPACK, brotli, NJS, Cookie-Flag, headers, ModSecurity with coreruleset
and BoringSSL with OCSP support. All built on the bleeding edge. Built on the
edge, for the edge.
Total size is only about ~47 MB uncompressed and ~12 MB compressed.
This is a fork of ranadeeppolavarapu/docker-nginx-http3. Thanks to him for doing the ground work.
Special in this fork:
- ModSecurity for nginx (SpiderLabs) with coreruleset
- HPACK enabled and nginx quiche patch by kn007/patch
- BoringSSL OCSP enabled with kn007/patch
- Removed nginx debug build
HTTP/3 support provided from the smart people at Cloudflare with the cloudflare/quiche project.
Images for this are available on Docker Hub and GHCR.
Docker Hub: docker pull patrikjuvonen/docker-nginx-http3
GitHub Container Registry (GHCR):
docker pull ghcr.io/patrikjuvonen/docker-nginx-http3
Semantic versioning is enabled since 519e20d7f65d53b976cf7d13e364dca326e988b7,
the first semantic version being 2.0.0. You can use a semantical version using tags
such as :x.y.z, :x.y, :x. I also provide a latest tag which is the latest
release, and master which is the latest image from master branch.
This is a base image like the default nginx image. It is meant to be used as a drop-in replacement for the nginx base image.
Best practice example Nginx configs are available in this repo. See nginx.conf and h3.nginx.conf.
Example:
# Base Nginx HTTP/3 Image
FROM patrikjuvonen/docker-nginx-http3:latest
# Copy your certs.
COPY localhost.key /etc/ssl/private/
COPY localhost.pem /etc/ssl/
# Copy your configs.
COPY nginx.conf /etc/nginx/
COPY h3.nginx.conf /etc/nginx/conf.d/H3 runs over UDP so, you will need to port map both TCP and UDP. Ex:
docker run -p 80:80 -p 443:443/tcp -p 443:443/udp ...
NOTE: Please note that you need a valid CA signed certificate for the client to upgrade you to HTTP/3. Let's Encrypt is a option for getting a free valid CA signed certificate.
Contributions are welcome. Please feel free to contribute 😊.
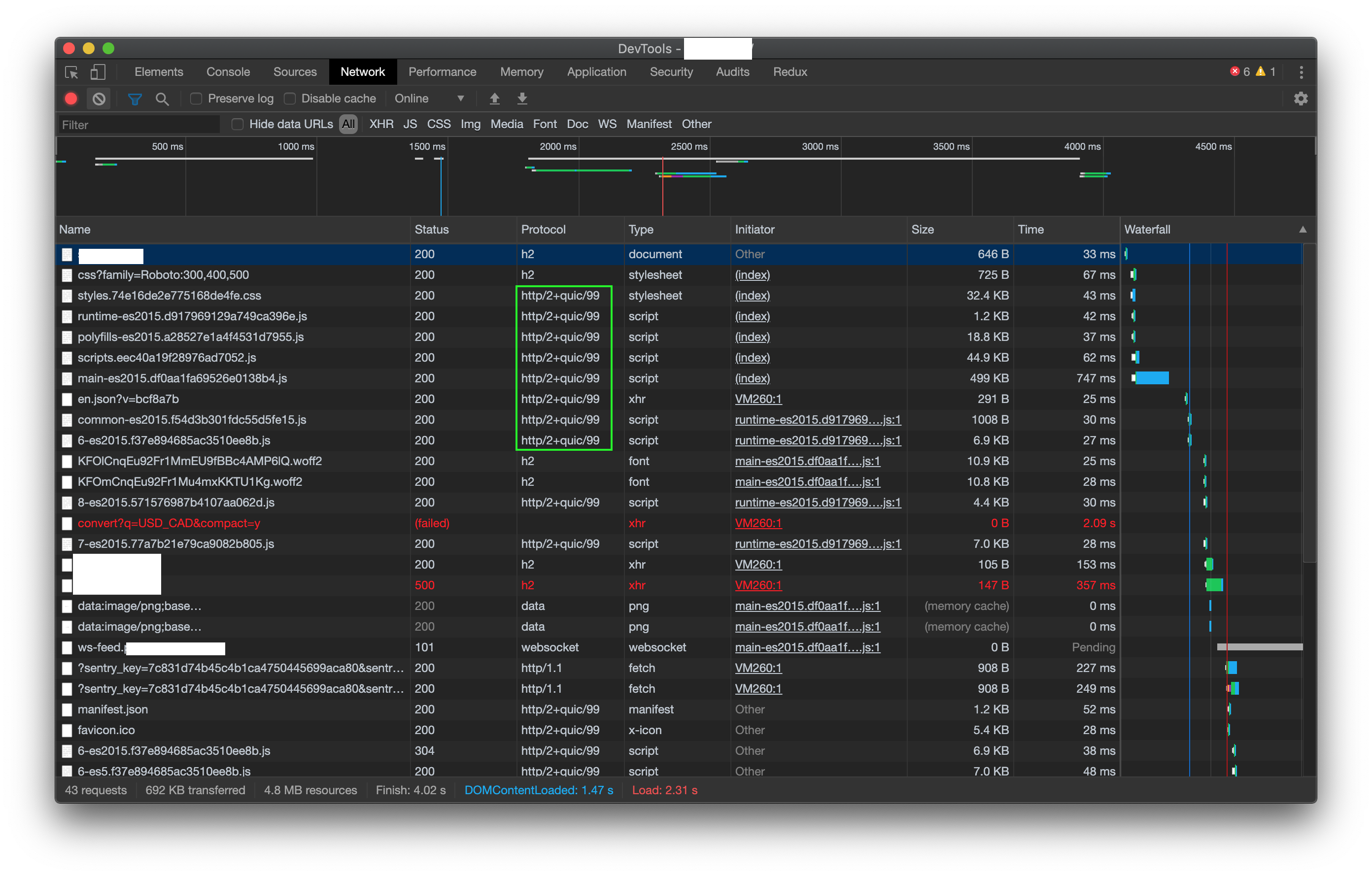
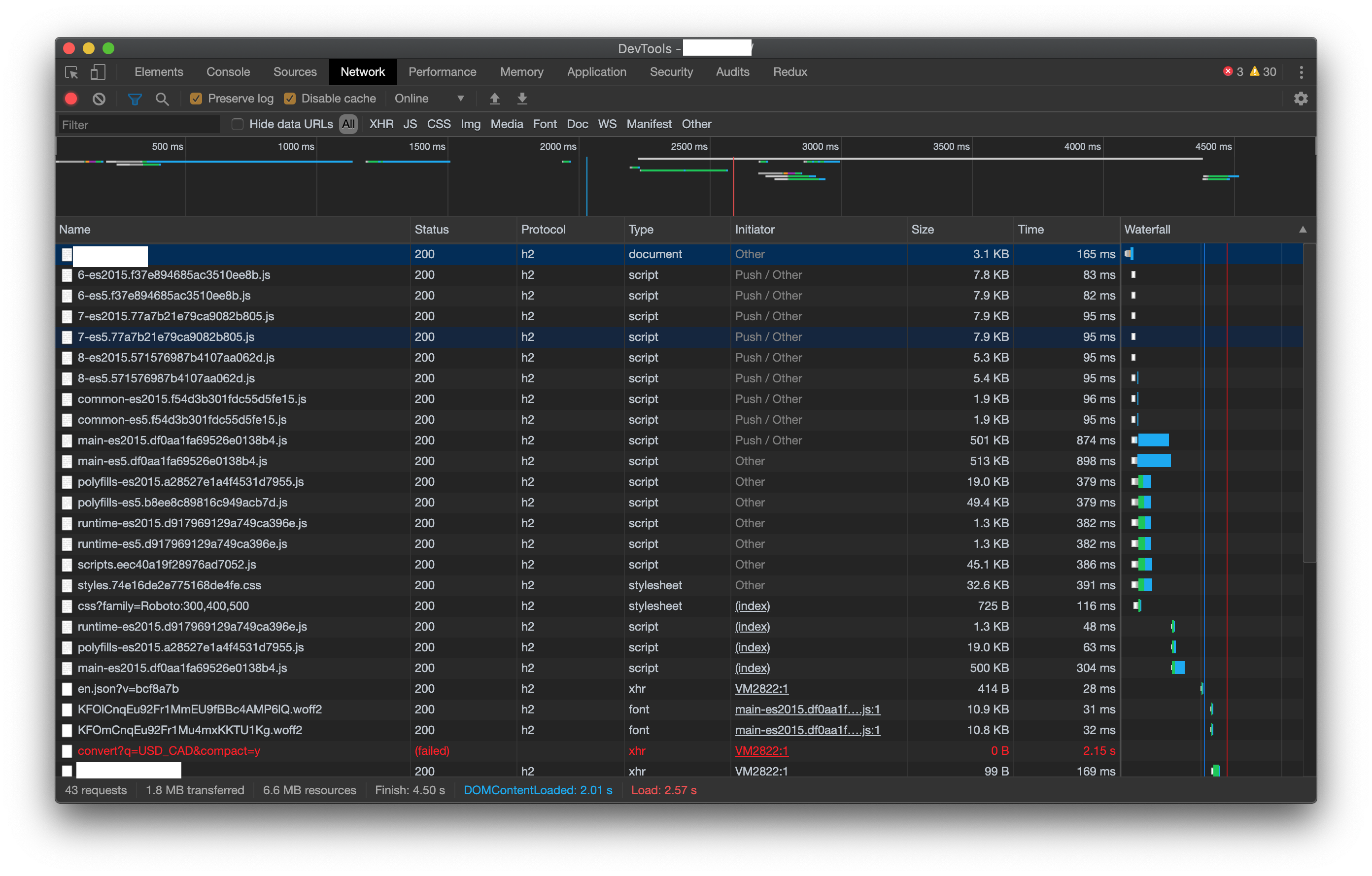
- HTTP/3 (QUIC) via Cloudflare's quiche
- HTTP/2 (with Server Push)
- HTTP/2
- BoringSSL (Google's flavor of OpenSSL)
- TLS 1.3 with 0-RTT support
- HPACK
- Brotli compression
- headers-more-nginx-module
- NJS
- nginx_cookie_flag_module
- PCRE latest with JIT compilation enabled
- zlib latest
- Alpine Linux (total size of 12 MB compressed)
- ModSecurity for nginx (SpiderLabs) with coreruleset
- HPACK enabled and nginx quiche patch by kn007/patch
- BoringSSL OCSP enabled with kn007/patch
- Removed nginx debug build
Possible additions in the future pending IETF spec approvals.
Using Chrome Canary with the following CLI flags:
--flag-switches-begin --enable-quic --quic-version=h3-29 --enable-features=EnableTLS13EarlyData --flag-switches-endRun on Mac OS (darwin):
"/Applications/Google Chrome Canary.app Contents/MacOS/Google Chrome Canary" \
--flag-switches-begin \
--enable-quic \
--quic-version=h3-29 \
--enable-features=EnableTLS13EarlyData \
--flag-switches-endWindows:
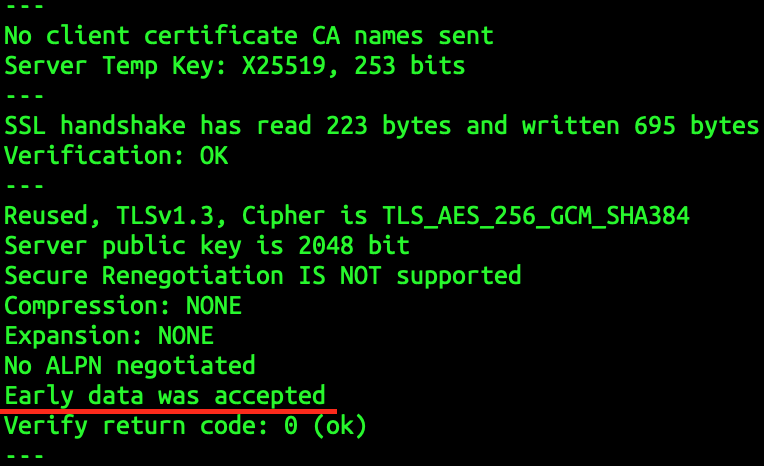
Since HTTP/3 is experimental, we have to be sensible with it. Therefore, below is HTTP/3 in production on one of my web apps 🙃.
host=domain.example.com # Replace your domain.
echo -e "GET / HTTP/1.1\r\nHost: $host\r\nConnection: close\r\n\r\n" > request.txt
openssl s_client -connect $host:443 -tls1_3 -sess_out session.pem -ign_eof < request.txt
openssl s_client -connect $host:443 -tls1_3 -sess_in session.pem -early_data request.txt