-
Notifications
You must be signed in to change notification settings - Fork 25
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Recursive resolver not setting ad bit -- unbound does.
#26
Comments
|
Digging into this with another (live) example: It looks like BNS is trying to compare an RRSIG for Why I think this affects only some subdomains:
The DNS zone from https://sitecheck.htools.work/check/e.xp : |
|
Checking out other validators like |
bns is just following a simple algorithm to recurse not handling many of the edge cases the fancy recursors deal with. It should keep track of zone cuts more carefully:
There's a delegation
We got an answer for We got a positive answer an SOA with the owner name being That means we need to find a trust path to this zone and then verify the RRSIGs. But also there's another way to tell without doing the SOA lookup notice the signer name for the A RRSIG is |
|
Didn't know about the RRSIG having the zone name, that's a clever way to identify them. Will try this method, thanks @buffrr |
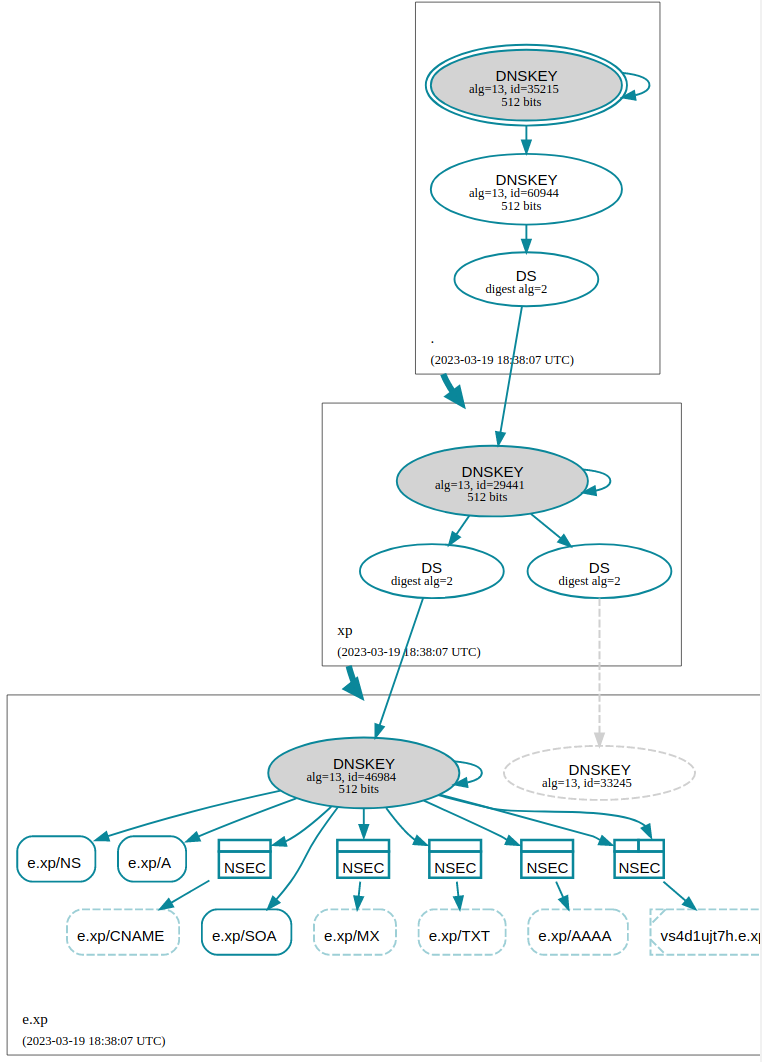
There's going to be a lot of logs in this post. In summary, running hsd with
--rs-no-unboundfails to verify the subdomainsebastian.rasorwhereas the unbound resolver does verify it:Invalid RRSIGs.Queries
--rs-no-unbound
with unbound
Logs --rs-no-unbound
The text was updated successfully, but these errors were encountered: